⭐ 가시다(gasida) 님이 진행하는 Terraform T101 4기 실습 스터디 게시글입니다.
책 '테라폼으로 시작하는 IaC'을 참고했습니다!
게시글 상 소스코드, 사진에서 **굵게** 혹은 '''코드쉘''' 에 대한 부분이 들어가있을수도 있습니다.1. Amazon EKS Blueprints for Terraform
EKS Blueprints 소개
- EKS Clsuter 를 쉽게 구성하게 해주는 운영 소프트웨어의 일종
- EKS Blueprints 를 사용하면 EKS환경(Control-plane, worker nodes, add-ons)에 필요한것들을 IaC 형태의 blueprints 로 구성할 수 있음.
- 쉽고 편하게 다양한 add-ons(e.g. Prometheus, ALB, Keda …) 를 배포할 수 있음
- ref: https://aws-quickstart.github.io/cdk-eks-blueprints/
Amazon EKS Blueprints Quick Start
Overview Welcome to the Amazon EKS Blueprints Quick Start documentation site. This repository contains the source code for the eks-blueprints NPM module. It can be used by AWS customers, partners, and internal AWS teams to configure and manage complete EKS
aws-quickstart.github.io
EKS Blueprints for Terraform
- Terraform 에 구현된 EKS Cluster Pattern(or snippet) 이 포함되어있고, AWS EKS 를 쉽고 빠르게 도입하는게 목적으로 하는 프로젝트
- ref: https://aws-ia.github.io/terraform-aws-eks-blueprints/
Amazon EKS Blueprints for Terraform
Amazon EKS Blueprints for Terraform Welcome to Amazon EKS Blueprints for Terraform! This project contains a collection of Amazon EKS cluster patterns implemented in Terraform that demonstrate how fast and easy it is for customers to adopt Amazon EKS. The p
aws-ia.github.io
특이사항
- EKS Blueprints for Terraform 에서 제공하는 코드를 그대로 사용해도되도록 의도한게 아님(가능하긴 함)
- Pattern or Snippets 은 Terraform Module 로 설계되지 않았음
- 특정정보가 필요한 경우(Route 53의 호스트영역ID, ACM 인증서 ARN) 만 variables 패턴을 사용
- 일반정보의 경우 local 블록을 통해 사용
- variables, outputs 을 최대한 노출하지 않음 + 파일 참조를 최대한 간소화시켰다
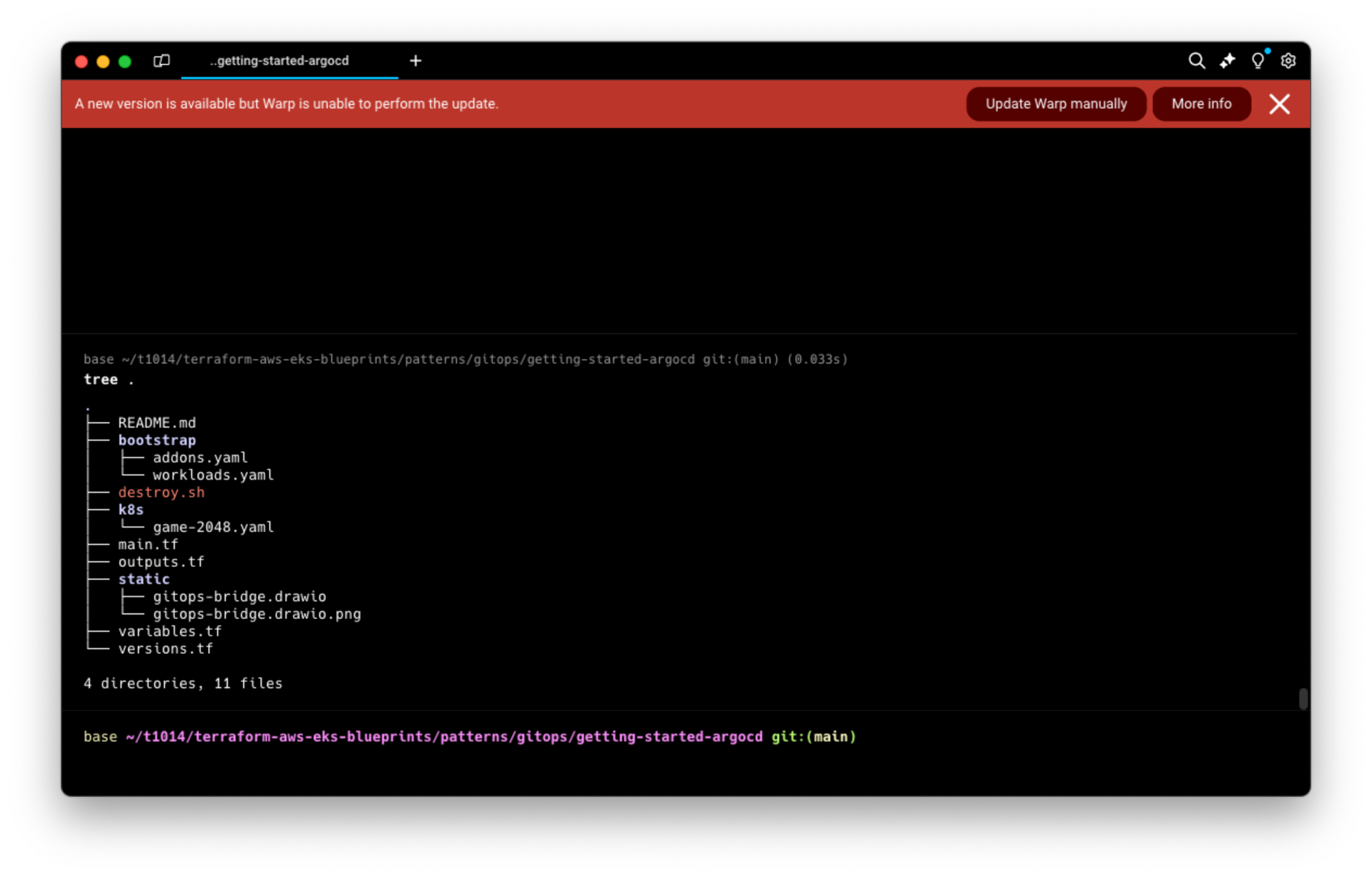
EKS Blueprints 지원을 위해 제작한 모듈
- terraform-aws-eks-blueprint-addon: IAM역할 외에도, Terraform resource 를 사용하여 Add-on을 프로비저닝 하는 모듈
- terraform-aws-eks-blueprint-addons: 여러개의 Add-on을 프로비저닝하는 모듈. terraform-aws-eks-blueprint-addon 모듈을 사용하는 Helm Chart 기반모듈
- terraform-aws-eks-blueprints-teams: 멀티테넌시(계정권한이 존재하는) 리소스를 프로비저닝하는 모듈
다양한 연관 프로젝트
- GitOps:
- terraform-aws-eks-ack-addons: EKS 에 ack controller 를 배포하기 위한 테라폼 Module
- crossplane-on-eks: Crossplane Compositions, Composite Resource Definitions 라이브러리를 사용해서 AWS 리소스를 프로비저닝하는 오픈소스
- Data on EKS
- data-on-eks: Amazon EKS 위에 데이터 워크로드를 프로비저닝하는 collection
- terraform-aws-eks-data-addons: Amazon EKS 위에 데이터 워크로드에서 사용하는 다중 add-ons 을 배포하는 테라폼 모듈
- Observability Accelerator
- Karpenter Blueprints
실습안내
- 다양한 Pattern에서 Consumption 섹션을 참조하면 배포하는게 가능함
- 일반적으로 프로비저닝할때에는 아래의 단계로 배포됨
terraform init terraform apply -target="module.vpc" -auto-approve terraform apply -target="module.eks" -auto-approve terraform apply -auto-approve- 모든 리소스가 성공적으로 프로비저닝되면 다음명령어를 사용하여 kubeconfig 를 업데이트할 수 있음
aws eks --region <REGION> update-kubeconfig --name <CLUSTER_NAME> --alias <CLUSTER_NAME>- 프로비저닝된 리소스를 제거할때에는 아래의 단계로 실행됨
terraform destroy -target="module.eks_blueprints_addons" -auto-approve terraform destroy -target="module.eks" -auto-approve terraform destroy -auto-approve- 실습환경 준비
#공식 깃허브 git clone https://github.com/aws-ia/terraform-aws-eks-blueprints #아래내용은 이미 존재한다고 가정 #awscli, kubectl, terraform
2. 실습: GitOps Getting Started(ArgoCD)
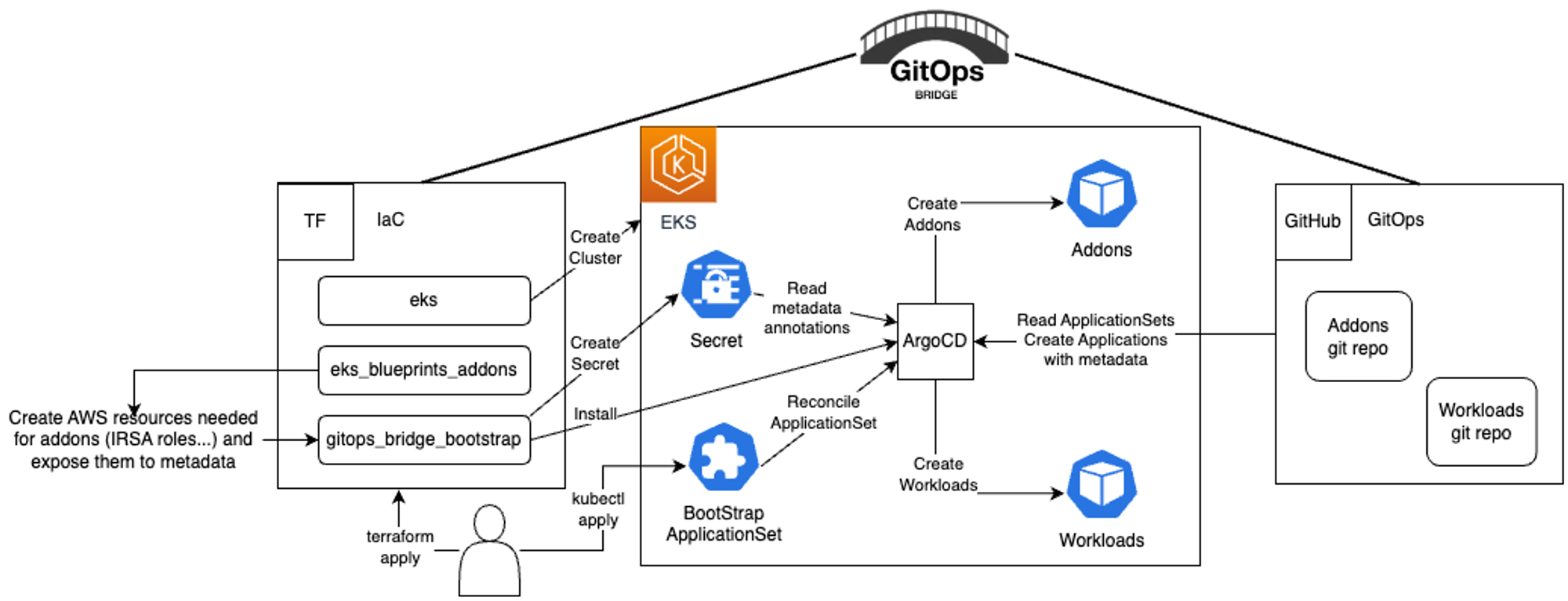
패턴실습설명
- GitOps Bridge 패턴을 통해 구성된 add-on 으로 EKS 를배포합니다
- GitOps Bridge Pattern: IaC(Infrastructure as Code)와 GitOps 사이의 차이를 메꾸는 패턴
- 실습 플로우
Terraform 으로 Cloud Resource 배포 Resource 의 Metadata를 ArgoCD Secret에 저장 GitOps 가 ArgoCD Secret 를 사용해 Helm 차트를 구성하여 배포
실습시작!
cd terraform-aws-eks-blueprints/patterns/gitops/getting-started-argocd
코드구성확인
main.tf
provider "aws" {
region = local.region
}
data "aws_caller_identity" "current" {}
data "aws_availability_zones" "available" {}
provider "helm" {
kubernetes {
host = module.eks.cluster_endpoint
cluster_ca_certificate = base64decode(module.eks.cluster_certificate_authority_data)
exec {
api_version = "client.authentication.k8s.io/v1beta1"
command = "aws"
# This requires the awscli to be installed locally where Terraform is executed
args = ["eks", "get-token", "--cluster-name", module.eks.cluster_name, "--region", local.region]
}
}
}
provider "kubernetes" {
host = module.eks.cluster_endpoint
cluster_ca_certificate = base64decode(module.eks.cluster_certificate_authority_data)
exec {
api_version = "client.authentication.k8s.io/v1beta1"
command = "aws"
# This requires the awscli to be installed locally where Terraform is executed
args = ["eks", "get-token", "--cluster-name", module.eks.cluster_name, "--region", local.region]
}
}
- 프로바이더 설정
- kubernetes 에 args 로 커맨드 명령어 지정한거에 주목
locals {
name = "getting-started-gitops"
region = var.region
cluster_version = var.kubernetes_version
vpc_cidr = var.vpc_cidr
azs = slice(data.aws_availability_zones.available.names, 0, 3)
gitops_addons_url = "${var.gitops_addons_org}/${var.gitops_addons_repo}"
gitops_addons_basepath = var.gitops_addons_basepath
gitops_addons_path = var.gitops_addons_path
gitops_addons_revision = var.gitops_addons_revision
gitops_workload_url = "${var.gitops_workload_org}/${var.gitops_workload_repo}"
gitops_workload_basepath = var.gitops_workload_basepath
gitops_workload_path = var.gitops_workload_path
gitops_workload_revision = var.gitops_workload_revision
aws_addons = {
enable_cert_manager = try(var.addons.enable_cert_manager, false)
enable_aws_efs_csi_driver = try(var.addons.enable_aws_efs_csi_driver, false)
enable_aws_fsx_csi_driver = try(var.addons.enable_aws_fsx_csi_driver, false)
enable_aws_cloudwatch_metrics = try(var.addons.enable_aws_cloudwatch_metrics, false)
enable_aws_privateca_issuer = try(var.addons.enable_aws_privateca_issuer, false)
enable_cluster_autoscaler = try(var.addons.enable_cluster_autoscaler, false)
enable_external_dns = try(var.addons.enable_external_dns, false)
enable_external_secrets = try(var.addons.enable_external_secrets, false)
enable_aws_load_balancer_controller = try(var.addons.enable_aws_load_balancer_controller, false)
enable_fargate_fluentbit = try(var.addons.enable_fargate_fluentbit, false)
enable_aws_for_fluentbit = try(var.addons.enable_aws_for_fluentbit, false)
enable_aws_node_termination_handler = try(var.addons.enable_aws_node_termination_handler, false)
enable_karpenter = try(var.addons.enable_karpenter, false)
enable_velero = try(var.addons.enable_velero, false)
enable_aws_gateway_api_controller = try(var.addons.enable_aws_gateway_api_controller, false)
enable_aws_ebs_csi_resources = try(var.addons.enable_aws_ebs_csi_resources, false)
enable_aws_secrets_store_csi_driver_provider = try(var.addons.enable_aws_secrets_store_csi_driver_provider, false)
enable_ack_apigatewayv2 = try(var.addons.enable_ack_apigatewayv2, false)
enable_ack_dynamodb = try(var.addons.enable_ack_dynamodb, false)
enable_ack_s3 = try(var.addons.enable_ack_s3, false)
enable_ack_rds = try(var.addons.enable_ack_rds, false)
enable_ack_prometheusservice = try(var.addons.enable_ack_prometheusservice, false)
enable_ack_emrcontainers = try(var.addons.enable_ack_emrcontainers, false)
enable_ack_sfn = try(var.addons.enable_ack_sfn, false)
enable_ack_eventbridge = try(var.addons.enable_ack_eventbridge, false)
}
oss_addons = {
enable_argocd = try(var.addons.enable_argocd, true)
enable_argo_rollouts = try(var.addons.enable_argo_rollouts, false)
enable_argo_events = try(var.addons.enable_argo_events, false)
enable_argo_workflows = try(var.addons.enable_argo_workflows, false)
enable_cluster_proportional_autoscaler = try(var.addons.enable_cluster_proportional_autoscaler, false)
enable_gatekeeper = try(var.addons.enable_gatekeeper, false)
enable_gpu_operator = try(var.addons.enable_gpu_operator, false)
enable_ingress_nginx = try(var.addons.enable_ingress_nginx, false)
enable_kyverno = try(var.addons.enable_kyverno, false)
enable_kube_prometheus_stack = try(var.addons.enable_kube_prometheus_stack, false)
enable_metrics_server = try(var.addons.enable_metrics_server, false)
enable_prometheus_adapter = try(var.addons.enable_prometheus_adapter, false)
enable_secrets_store_csi_driver = try(var.addons.enable_secrets_store_csi_driver, false)
enable_vpa = try(var.addons.enable_vpa, false)
}
addons = merge(
local.aws_addons,
local.oss_addons,
{ kubernetes_version = local.cluster_version },
{ aws_cluster_name = module.eks.cluster_name }
)
addons_metadata = merge(
module.eks_blueprints_addons.gitops_metadata,
{
aws_cluster_name = module.eks.cluster_name
aws_region = local.region
aws_account_id = data.aws_caller_identity.current.account_id
aws_vpc_id = module.vpc.vpc_id
},
{
addons_repo_url = local.gitops_addons_url
addons_repo_basepath = local.gitops_addons_basepath
addons_repo_path = local.gitops_addons_path
addons_repo_revision = local.gitops_addons_revision
},
{
workload_repo_url = local.gitops_workload_url
workload_repo_basepath = local.gitops_workload_basepath
workload_repo_path = local.gitops_workload_path
workload_repo_revision = local.gitops_workload_revision
}
)
tags = {
Blueprint = local.name
GithubRepo = "github.com/aws-ia/terraform-aws-eks-blueprints"
}
}
- 기타 애드온 설정
################################################################################
# GitOps Bridge: Bootstrap
################################################################################
module "gitops_bridge_bootstrap" {
source = "github.com/gitops-bridge-dev/gitops-bridge-argocd-bootstrap-terraform?ref=v2.0.0"
cluster = {
metadata = local.addons_metadata
addons = local.addons
}
}
- GitOps Bridge를 설정하여 ArgoCD 를 부트스트래핑 진행함
################################################################################
# EKS Blueprints Addons
################################################################################
module "eks_blueprints_addons" {
source = "aws-ia/eks-blueprints-addons/aws"
version = "~> 1.0"
cluster_name = module.eks.cluster_name
cluster_endpoint = module.eks.cluster_endpoint
cluster_version = module.eks.cluster_version
oidc_provider_arn = module.eks.oidc_provider_arn
# Using GitOps Bridge
create_kubernetes_resources = false
# EKS Blueprints Addons
enable_cert_manager = local.aws_addons.enable_cert_manager
enable_aws_efs_csi_driver = local.aws_addons.enable_aws_efs_csi_driver
enable_aws_fsx_csi_driver = local.aws_addons.enable_aws_fsx_csi_driver
enable_aws_cloudwatch_metrics = local.aws_addons.enable_aws_cloudwatch_metrics
enable_aws_privateca_issuer = local.aws_addons.enable_aws_privateca_issuer
enable_cluster_autoscaler = local.aws_addons.enable_cluster_autoscaler
enable_external_dns = local.aws_addons.enable_external_dns
enable_external_secrets = local.aws_addons.enable_external_secrets
enable_aws_load_balancer_controller = local.aws_addons.enable_aws_load_balancer_controller
enable_fargate_fluentbit = local.aws_addons.enable_fargate_fluentbit
enable_aws_for_fluentbit = local.aws_addons.enable_aws_for_fluentbit
enable_aws_node_termination_handler = local.aws_addons.enable_aws_node_termination_handler
enable_karpenter = local.aws_addons.enable_karpenter
enable_velero = local.aws_addons.enable_velero
enable_aws_gateway_api_controller = local.aws_addons.enable_aws_gateway_api_controller
tags = local.tags
}
################################################################################
# EKS Cluster
################################################################################
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
cluster_name = local.name
cluster_version = local.cluster_version
cluster_endpoint_public_access = true
vpc_id = module.vpc.vpc_id
subnet_ids = module.vpc.private_subnets
eks_managed_node_groups = {
initial = {
instance_types = ["m5.large"]
min_size = 1
max_size = 3
desired_size = 2
}
}
# EKS Addons
cluster_addons = {
coredns = {}
kube-proxy = {}
vpc-cni = {
# Specify the VPC CNI addon should be deployed before compute to ensure
# the addon is configured before data plane compute resources are created
# See README for further details
before_compute = true
most_recent = true # To ensure access to the latest settings provided
configuration_values = jsonencode({
env = {
# Reference docs https://docs.aws.amazon.com/eks/latest/userguide/cni-increase-ip-addresses.html
ENABLE_PREFIX_DELEGATION = "true"
WARM_PREFIX_TARGET = "1"
}
})
}
}
tags = local.tags
}
- eks 리소스 정보(클러스터 스펙, 노드그룹)
################################################################################
# Supporting Resources
################################################################################
module "vpc" {
source = "terraform-aws-modules/vpc/aws"
version = "~> 5.0"
name = local.name
cidr = local.vpc_cidr
azs = local.azs
private_subnets = [for k, v in local.azs : cidrsubnet(local.vpc_cidr, 4, k)]
public_subnets = [for k, v in local.azs : cidrsubnet(local.vpc_cidr, 8, k + 48)]
enable_nat_gateway = true
single_nat_gateway = true
public_subnet_tags = {
"kubernetes.io/role/elb" = 1
}
private_subnet_tags = {
"kubernetes.io/role/internal-elb" = 1
}
tags = local.tags
}
- VPC 정보(서브넷)
variables.tf
variable "vpc_cidr" {
description = "VPC CIDR"
type = string
default = "10.0.0.0/16"
}
variable "region" {
description = "AWS region"
type = string
default = "us-west-2"
}
variable "kubernetes_version" {
description = "Kubernetes version"
type = string
default = "1.28"
}
variable "addons" {
description = "Kubernetes addons"
type = any
default = {
enable_aws_load_balancer_controller = true
enable_metrics_server = true
}
}
# Addons Git
variable "gitops_addons_org" {
description = "Git repository org/user contains for addons"
type = string
default = "https://github.com/aws-samples"
}
variable "gitops_addons_repo" {
description = "Git repository contains for addons"
type = string
default = "eks-blueprints-add-ons"
}
variable "gitops_addons_revision" {
description = "Git repository revision/branch/ref for addons"
type = string
default = "main"
}
variable "gitops_addons_basepath" {
description = "Git repository base path for addons"
type = string
default = "argocd/"
}
variable "gitops_addons_path" {
description = "Git repository path for addons"
type = string
default = "bootstrap/control-plane/addons"
}
# Workloads Git
variable "gitops_workload_org" {
description = "Git repository org/user contains for workload"
type = string
default = "https://github.com/aws-ia"
}
variable "gitops_workload_repo" {
description = "Git repository contains for workload"
type = string
default = "terraform-aws-eks-blueprints"
}
variable "gitops_workload_revision" {
description = "Git repository revision/branch/ref for workload"
type = string
default = "main"
}
variable "gitops_workload_basepath" {
description = "Git repository base path for workload"
type = string
default = "patterns/gitops/"
}
variable "gitops_workload_path" {
description = "Git repository path for workload"
type = string
default = "getting-started-argocd/k8s"
}
- 사용하는 region 이 us-west-2 로 구성되어있습니다
outputs.tf
output "configure_kubectl" {
description = "Configure kubectl: make sure you're logged in with the correct AWS profile and run the following command to update your kubeconfig"
value = <<-EOT
export KUBECONFIG="/tmp/${module.eks.cluster_name}"
aws eks --region ${local.region} update-kubeconfig --name ${module.eks.cluster_name}
EOT
}
output "configure_argocd" {
description = "Terminal Setup"
value = <<-EOT
export KUBECONFIG="/tmp/${module.eks.cluster_name}"
aws eks --region ${local.region} update-kubeconfig --name ${module.eks.cluster_name}
export ARGOCD_OPTS="--port-forward --port-forward-namespace argocd --grpc-web"
kubectl config set-context --current --namespace argocd
argocd login --port-forward --username admin --password $(argocd admin initial-password | head -1)
echo "ArgoCD Username: admin"
echo "ArgoCD Password: $(kubectl get secrets argocd-initial-admin-secret -n argocd --template="{{index .data.password | base64decode}}")"
echo Port Forward: http://localhost:8080
kubectl port-forward -n argocd svc/argo-cd-argocd-server 8080:80
EOT
}
output "access_argocd" {
description = "ArgoCD Access"
value = <<-EOT
export KUBECONFIG="/tmp/${module.eks.cluster_name}"
aws eks --region ${local.region} update-kubeconfig --name ${module.eks.cluster_name}
echo "ArgoCD Username: admin"
echo "ArgoCD Password: $(kubectl get secrets argocd-initial-admin-secret -n argocd --template="{{index .data.password | base64decode}}")"
echo "ArgoCD URL: https://$(kubectl get svc -n argocd argo-cd-argocd-server -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')"
EOT
}
- value 에 EOT 로 쉘스크립트 입력받게 해놓은거 같음
bootstrap/addons.yaml
apiVersion: argoproj.io/v1alpha1
kind: ApplicationSet
metadata:
name: cluster-addons
namespace: argocd
spec:
syncPolicy:
preserveResourcesOnDeletion: true
generators:
- clusters: {}
template:
metadata:
name: cluster-addons
spec:
project: default
source:
repoURL: '{{metadata.annotations.addons_repo_url}}'
path: '{{metadata.annotations.addons_repo_basepath}}{{metadata.annotations.addons_repo_path}}'
targetRevision: '{{metadata.annotations.addons_repo_revision}}'
directory:
recurse: true
destination:
namespace: argocd
name: '{{name}}'
syncPolicy:
automated: {}
- cluster add on 에 대한 설정
bootstrap/workloads.yaml
apiVersion: argoproj.io/v1alpha1
kind: ApplicationSet
metadata:
name: workloads
namespace: argocd
spec:
syncPolicy:
preserveResourcesOnDeletion: true
generators:
- clusters: {}
template:
metadata:
name: workloads
finalizers:
# This finalizer is for demo purposes, in production remove apps using argocd CLI "argocd app delete workload --cascade"
# When you invoke argocd app delete with --cascade, the finalizer is added automatically.
- resources-finalizer.argocd.argoproj.io
spec:
project: default
source:
repoURL: '{{metadata.annotations.workload_repo_url}}'
path: '{{metadata.annotations.workload_repo_basepath}}{{metadata.annotations.workload_repo_path}}'
targetRevision: '{{metadata.annotations.workload_repo_revision}}'
destination:
name: '{{name}}'
syncPolicy:
automated:
allowEmpty: true
syncOptions:
- CreateNamespace=true
retry:
limit: 60
배포
terraform init
terraform apply -target="module.vpc" -auto-approve
terraform apply -target="module.eks" -auto-approve
terraform apply -auto-approve- 단계적으로 배포하는 이유: VPC → EKS → 전체리소스 순으로 배포함으로써 리소스간 의존성을명확하게 만들 수 있다.
- EKS 는 VPC를 설정하여 배포하는 형태로 구성되어있음.
배포결과
Outputs:
access_argocd = <<EOT
export KUBECONFIG="/tmp/getting-started-gitops"
aws eks --region us-west-2 update-kubeconfig --name getting-started-gitops
echo "ArgoCD Username: admin"
echo "ArgoCD Password: $(kubectl get secrets argocd-initial-admin-secret -n argocd --template="{{index .data.password | base64decode}}")"
echo "ArgoCD URL: https://$(kubectl get svc -n argocd argo-cd-argocd-server -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')"
EOT
configure_argocd = <<EOT
export KUBECONFIG="/tmp/getting-started-gitops"
aws eks --region us-west-2 update-kubeconfig --name getting-started-gitops
export ARGOCD_OPTS="--port-forward --port-forward-namespace argocd --grpc-web"
kubectl config set-context --current --namespace argocd
argocd login --port-forward --username admin --password $(argocd admin initial-password | head -1)
echo "ArgoCD Username: admin"
echo "ArgoCD Password: $(kubectl get secrets argocd-initial-admin-secret -n argocd --template="{{index .data.password | base64decode}}")"
echo Port Forward: http://localhost:8080
kubectl port-forward -n argocd svc/argo-cd-argocd-server 8080:80
EOT
configure_kubectl = <<EOT
export KUBECONFIG="/tmp/getting-started-gitops"
aws eks --region us-west-2 update-kubeconfig --name getting-started-gitops
EOT
배포가 완료되면 아래명령어로 kubeconfig를 임시등록하여 저장합니다.
terraform output -raw configure_kubectl
#출력
export KUBECONFIG="/tmp/getting-started-gitops"
aws eks --region us-west-2 update-kubeconfig --name getting-started-gitops
#만약 kubeconfig 등록을 원한다면
aws eks --region <REGION> update-kubeconfig --name <CLUSTER_NAME> --alias <CLUSTER_NAME>
#<REGION> : us-west-2
#<CLUSTER_NAME> : getting-started-gitops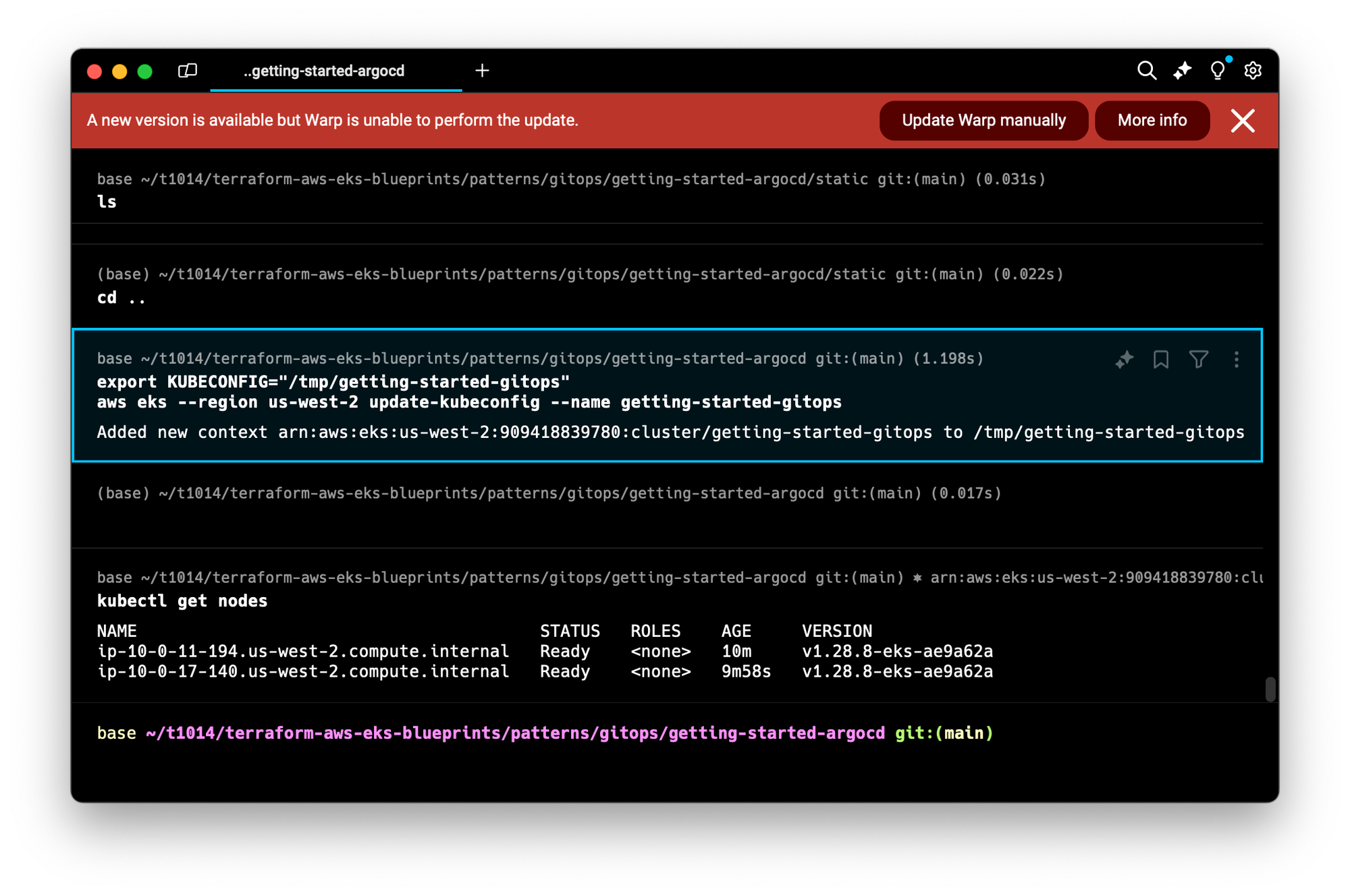
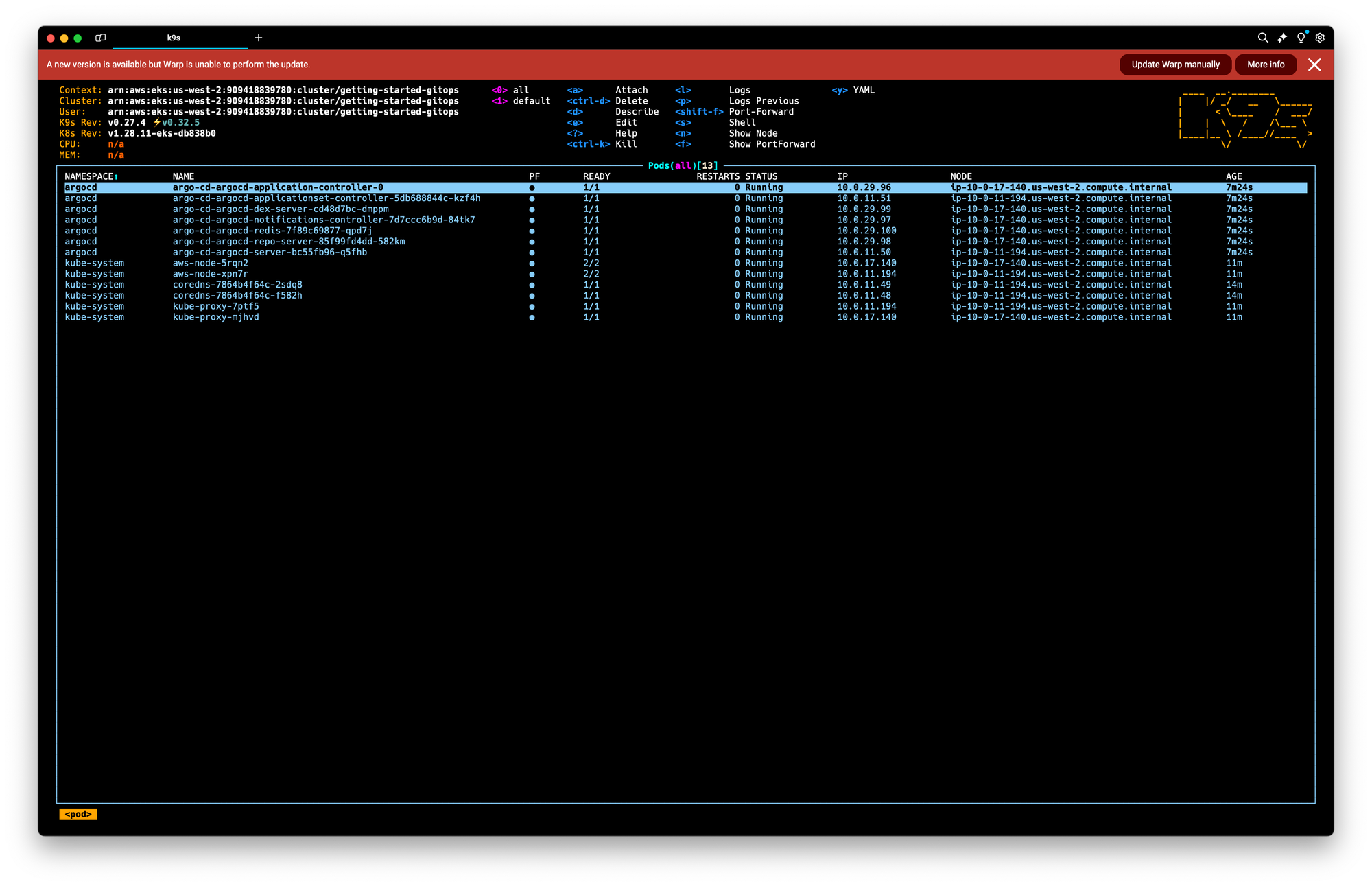
ArgoCD Secret 에 GitOps Bridge Pattern Metadata 를 추가
kubectl get secret -n argocd -l argocd.argoproj.io/secret-type=cluster -o json | jq '.items[0].metadata.annotations'
#출력
{
"addons_repo_basepath": "argocd/",
"addons_repo_path": "bootstrap/control-plane/addons",
"addons_repo_revision": "main",
"addons_repo_url": "https://github.com/aws-samples/eks-blueprints-add-ons",
"aws_account_id": "909418839780",
"aws_cluster_name": "getting-started-gitops",
"aws_load_balancer_controller_iam_role_arn": "arn:aws:iam::909418839780:role/alb-controller-20240727174241361300000002",
"aws_load_balancer_controller_namespace": "kube-system",
"aws_load_balancer_controller_service_account": "aws-load-balancer-controller-sa",
"aws_region": "us-west-2",
"aws_vpc_id": "vpc-02c1789f2dfaf2856",
"cluster_name": "in-cluster",
"environment": "dev",
"workload_repo_basepath": "patterns/gitops/",
"workload_repo_path": "getting-started-argocd/k8s",
"workload_repo_revision": "main",
"workload_repo_url": "https://github.com/aws-ia/terraform-aws-eks-blueprints"
}ArgoCD Addon 배포
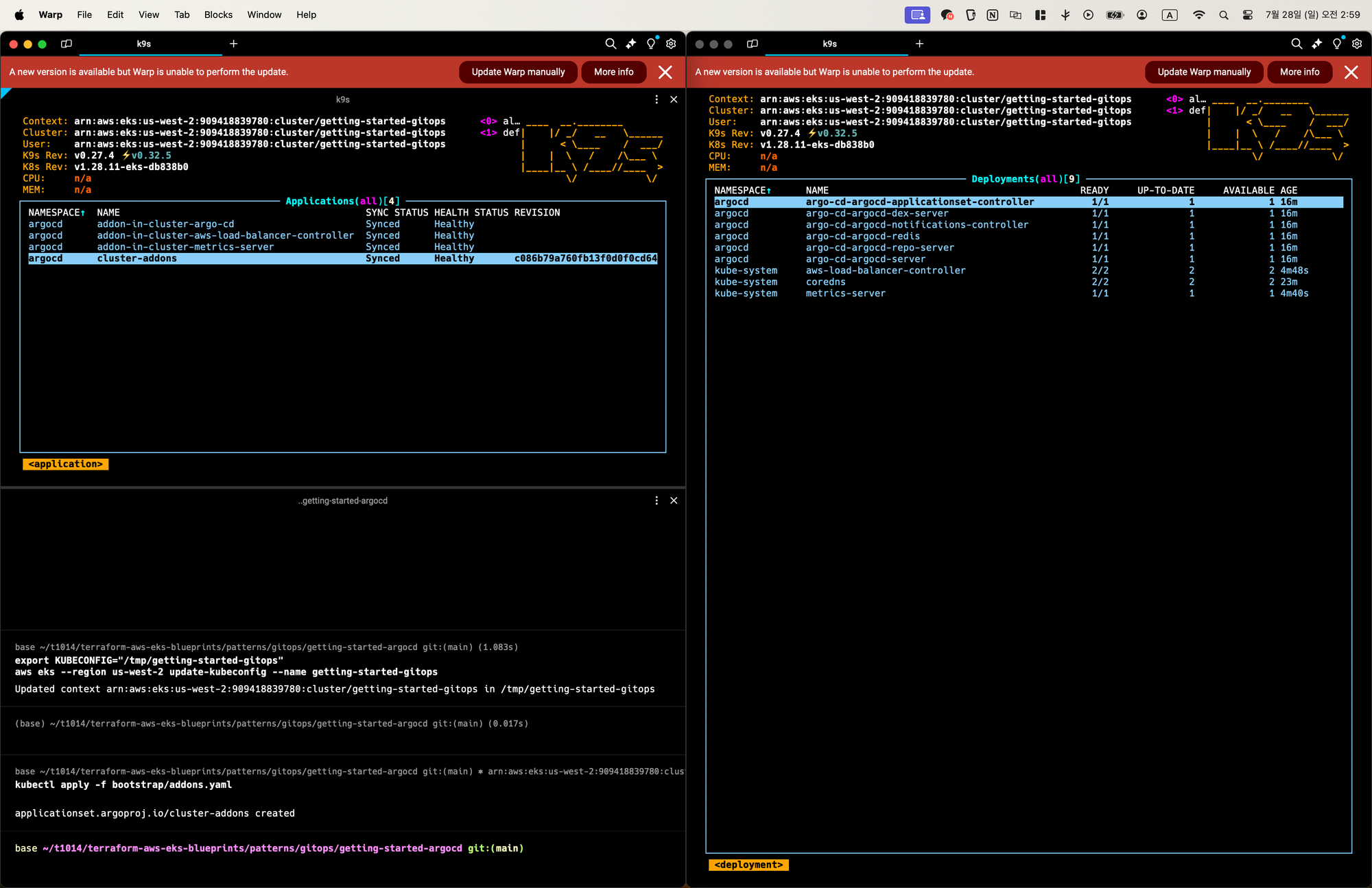
kubectl apply -f bootstrap/addons.yamlApplications이 모두 Synced가 될때까지 대기
- Applications 은 GitOps Pattern에서 사용하는 CRD의 일종(Custom Definition Object)
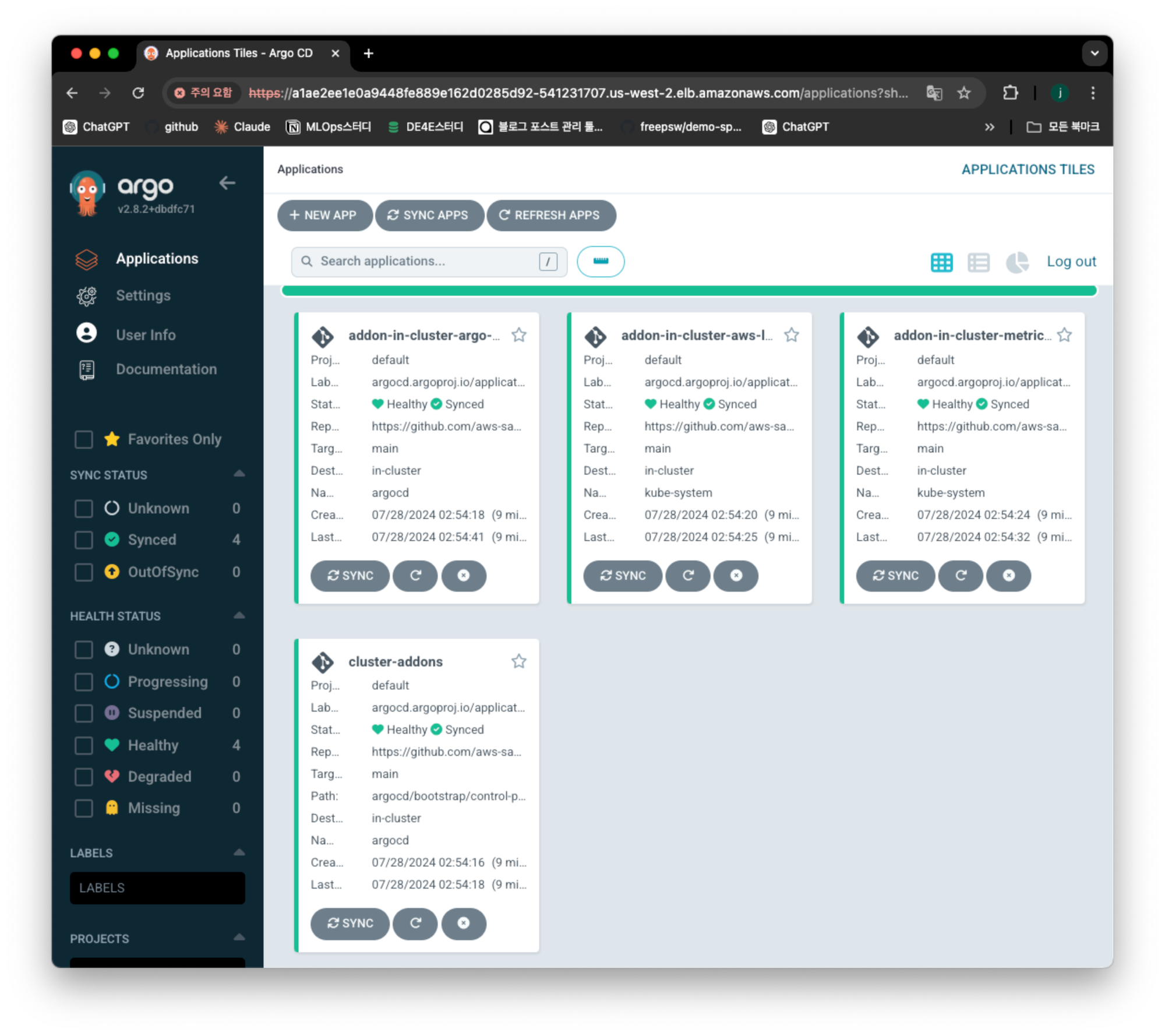
ArgoCD UI 액세스
terraform output -raw access_argocdexport KUBECONFIG="/tmp/getting-started-gitops"
aws eks --region us-west-2 update-kubeconfig --name getting-started-gitops
echo "ArgoCD Username: admin"
echo "ArgoCD Password: $(kubectl get secrets argocd-initial-admin-secret -n argocd --template="{{index .data.password | base64decode}}")"
echo "ArgoCD URL: https://$(kubectl get svc -n argocd argo-cd-argocd-server -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')"나의 경우에는 아래처럼 나왔고, URL 로 접속해보기
ArgoCD Username: admin
ArgoCD Password: hVOUwo2oXDh8vBdf
ArgoCD URL: https://a1ae2ee1e0a9448fe889e162d0285d92-541231707.us-west-2.elb.amazonaws.com
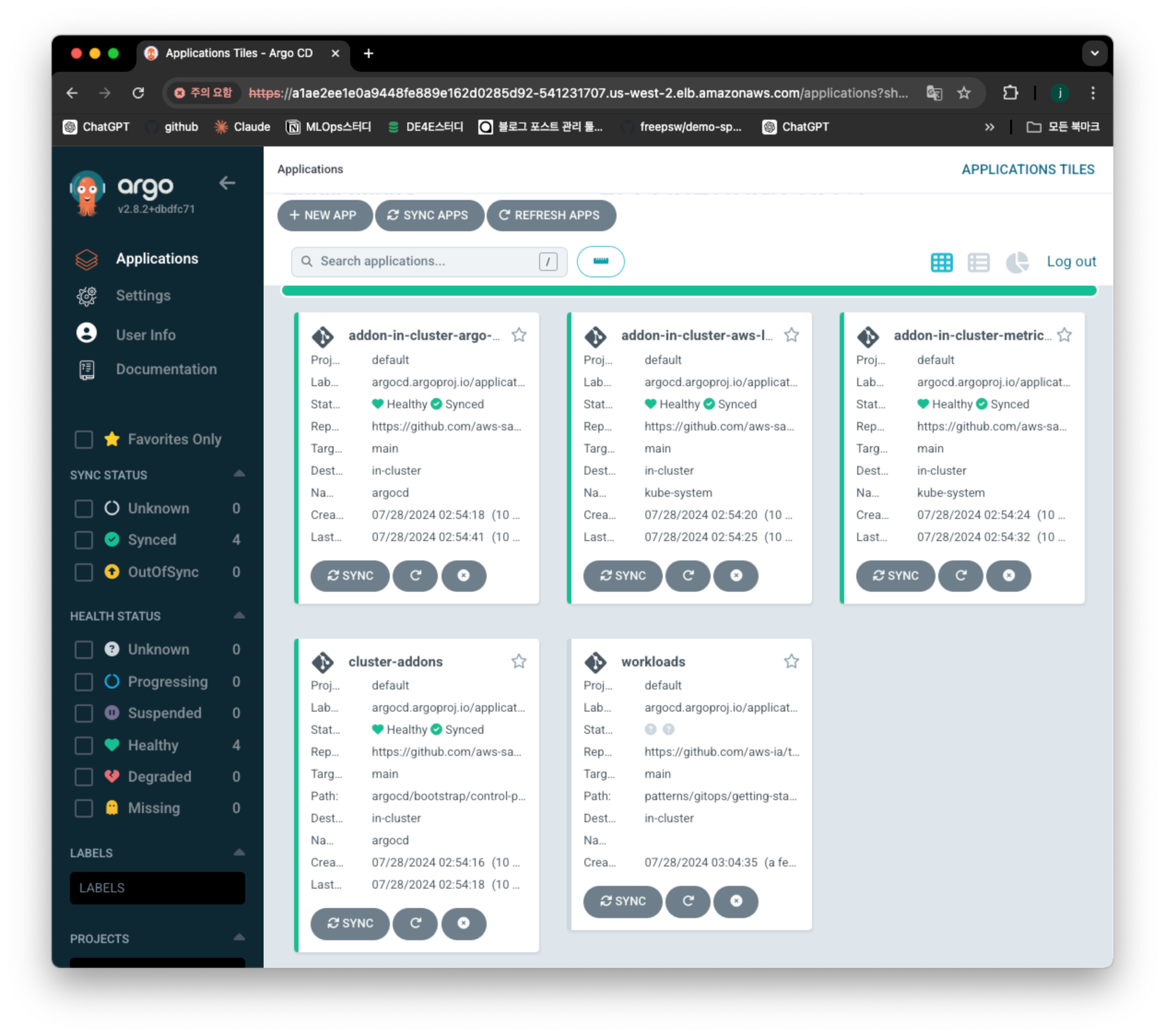
예제 컨테이너 배포
kubectl apply -f bootstrap/workloads.yaml
#k8s/game-2048
배포한바로직후사진. Application 에 먼저 배포된 이후, Deployment에 적용된다
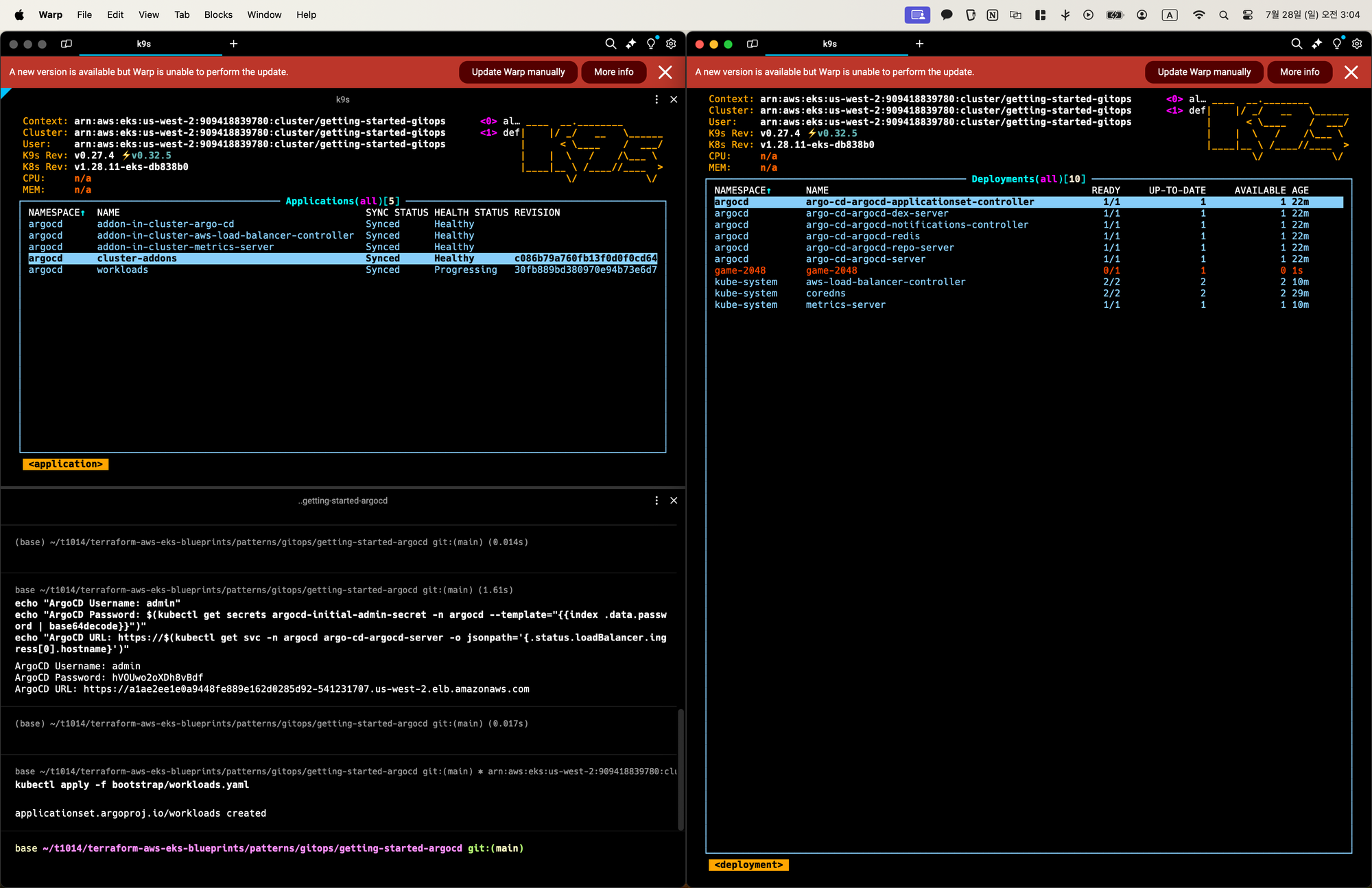
배포결과확인
kubectl get -n game-2048 deployments,service,ep,ingress
#출력
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/game-2048 1/1 1 1 108s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/game-2048 ClusterIP 172.20.193.180 <none> 80/TCP 108s
NAME ENDPOINTS AGE
endpoints/game-2048 10.0.25.240:80 108s
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress.networking.k8s.io/game-2048 alb * k8s-game2048-game2048-2e55885dbe-1191415183.us-west-2.elb.amazonaws.com 80 108sALB를 통해 어플리케이션 액세스
Endpoint 정보 확인
kubectl exec -n game-2048 deploy/game-2048 -- \
wget -S --spider $(kubectl get -n game-2048 ingress game-2048 -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')
#출력
Connecting to k8s-game2048-game2048-2e55885dbe-1191415183.us-west-2.elb.amazonaws.com (34.223.186.90:80)
HTTP/1.1 200 OK
Date: Sat, 27 Jul 2024 18:08:30 GMT
Content-Type: text/html
Content-Length: 3988
Connection: close
Server: nginx
Last-Modified: Wed, 06 Oct 2021 17:35:37 GMT
ETag: "615dde69-f94"
Accept-Ranges: bytes
remote file exists이 중에서 상단 Connecting to 이후 나오는 문자열이 ALB를 통해 배포된 2048 게임
#html 링크만 확인해보려면
echo "Application URL: http://$(kubectl get -n game-2048 ingress game-2048 -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')"
(진짜 됨)
실습종료및 리소스제거하는 명령어
./destroy.sh'외부활동' 카테고리의 다른 글
| [KANS3] Docker (2) | 2024.09.01 |
|---|---|
| [T101] 4기 스터디: OpenTofu (1) | 2024.08.03 |
| [T101] 4기 스터디: Module (3) | 2024.07.14 |
| [T101] 4기 스터디: Confluent Cloud with Terraform (0) | 2024.06.29 |
| [AEWS] 2기 스터디: Terraform (0) | 2024.04.28 |
